The Black Basta ransomware-as-a-service (RaaS) group made more than US $100 million in ransoms and targeted at least 580 entities during its reign between 2021 and early 2025. It made this extraordinary amount of money in part by its recruitment and employment of experienced cybercrime players who had honed their skills. The group’s leader, the actor tramp, who was tangentially linked to the Conti ransomware group, had extensive contacts into this criminal ecosystem. These insights were revealed in February 2025 when an unknown person going by the nickname ExploitWhispers leaked 197,000 chat messages belonging to the group that covered a nearly one-year period between Sept. 18, 2023, and Sept. 28, 2024.
One of tramp’s trust lieutenants was a threat actor who went by the moniker tinker. The actor tinker joined Black Basta in late 2023 primarily as a creative director. This seems an odd position for a ransomware gang, but there was a clear role for tinker: the threat actor was good at generating original ideas. The threat actor also had specific experience in running needed functions of a ransomware group to perform at scale, ranging from operating call centers, drafting phishing content and strong-arming ransomware victims through coercion. The Black Basta chat logs documented conversations between tinker and tramp (who went by the name usernamegg in the chats) between Dec. 18, 2023, and June 16, 2024. This blog post will explore the critical services tinker provided to Black Basta and why those skills were valuable.
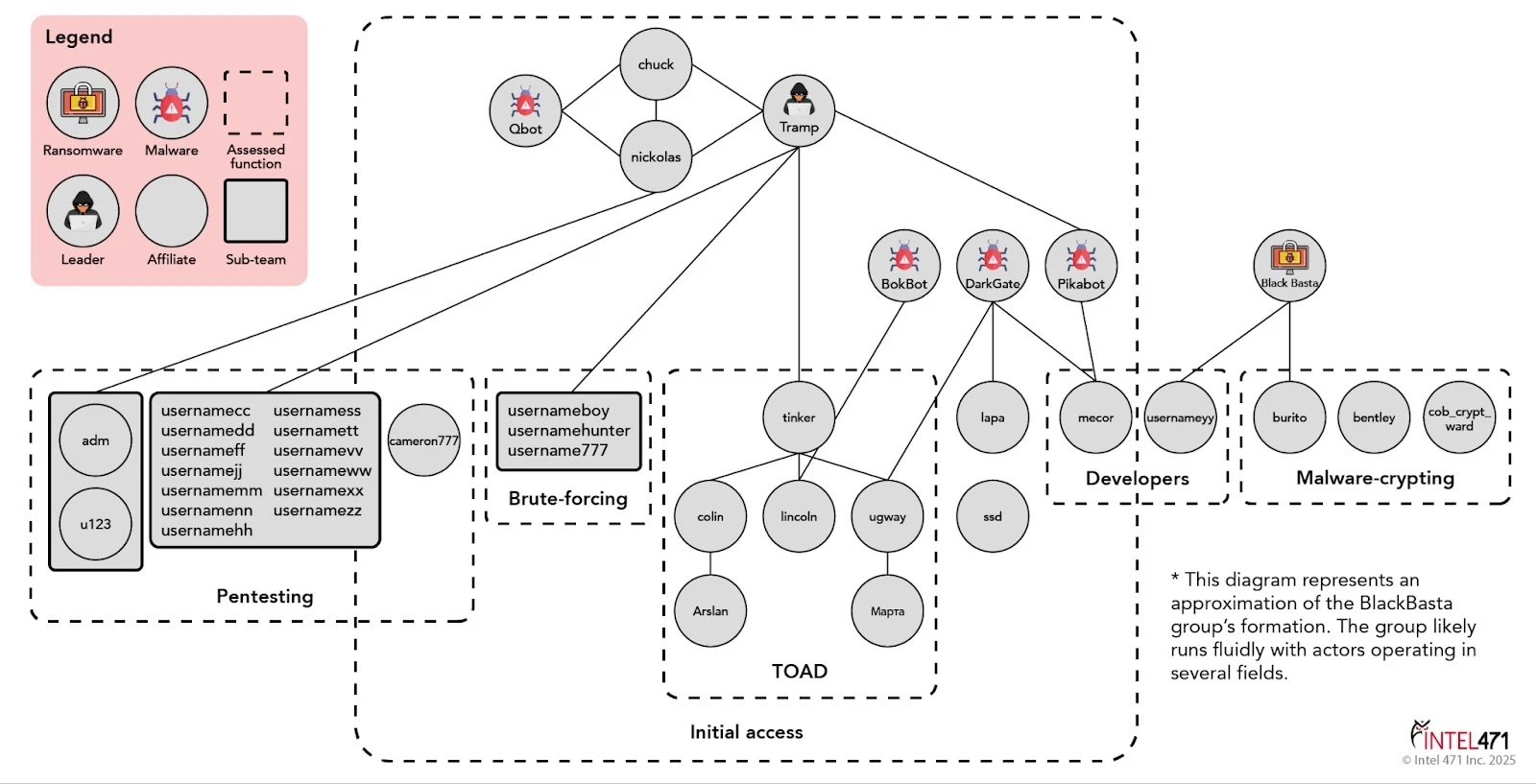
The Black Basta group was in a rare echelon of prolific cybercriminal extortion gangs due to the number of attacks it executed and ransoms gained. With most of its members likely located in Russia and safely out of reach of Western law enforcement, this group achieved that scale by adopting the practices of successful predecessors, such as the Conti, Maze and REvil ransomware groups. Like Conti, Black Basta ran call centers where specialists were tasked with social engineering victims into installing software that would lead to infections. It had penetration testers, software developers and malware crypters, which specialized in making malware undetectable. The group extensively researched potential victims and their revenues and refined extortion strategies to maximize payouts. The actor tinker played an important role in securing initial access to organizations. In order to maintain high ransom revenues, the gang needed a steady supply of compromised organizations where it had footholds.
This chart shows how Black Basta threat actors were segmented into specialized teams with specific roles in conducting and enabling ransomware attacks at scale. The actor tinker is seen in telephone-oriented attack delivery (TOAD), a technique that involves calling or receiving calls from victims in order to gain access.
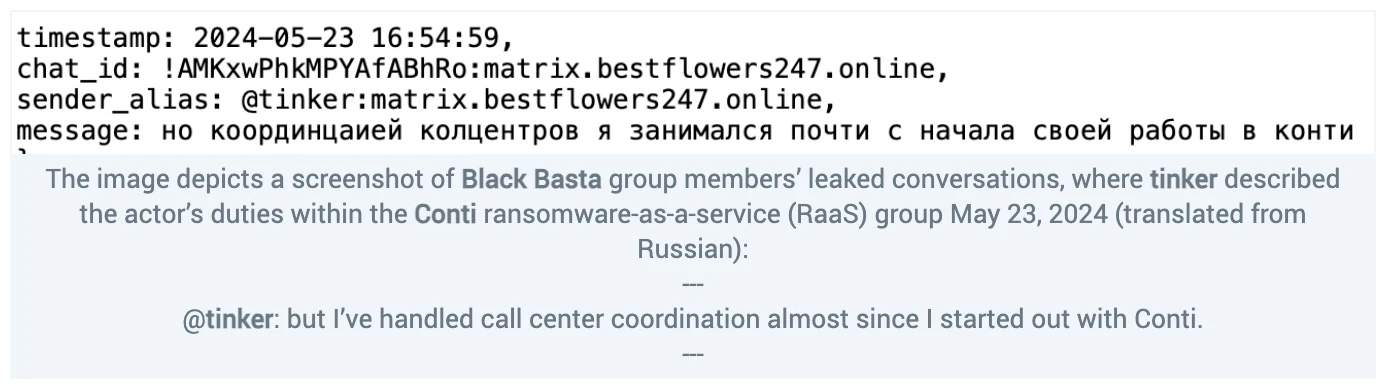
After tinker joined Black Basta and began writing in the chats, the actor disclosed experience running call centers, including for the Conti group:
The Conti ransomware group disbanded in early 2022. The group, which had been the most prolific RaaS for about two years, faced several headwinds, including becoming too well known. The group and its affiliates executed significant attacks against Costa Rica and Ireland’s Health Service Executive that drew the attention of Western countries that were increasingly becoming frustrated with ransomware and exploring more aggressive ways to disrupt it. The group expressed support for Russia after its full-scale invasion of Ukraine in February 2022, which put it at odds with Ukrainian cybercrime actors who had often collaborated closely with Russian ones. Following its public expression of support for Russia, Conti saw at least 60,000 chat messages from its servers leaked by a Ukrainian researcher. As a result, tinker moved on from Conti to one of its spinoffs, the BlackSuit aka Royal ransomware group where tinker worked as a negotiator.
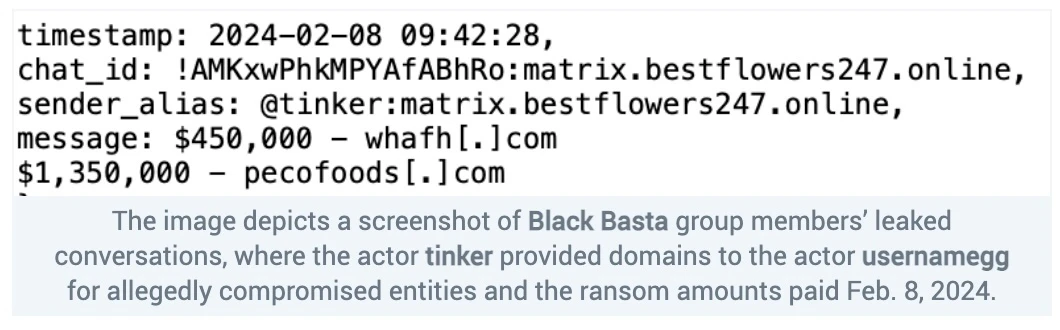
The actor appeared to manage Black Basta’s data leak site initially. Ransomware groups use these sites to publish stolen data. If an organization doesn’t need a decryption key for locked up data, ransomware gangs continue to put on the heat by threatening to publish it. This often results in a ransom. In early November 2023, tramp told another Black Basta member, usernameyy, that tinker had visibility into “almost” all ongoing ransomware campaigns, which apparently meant tinker was negotiating with victims.
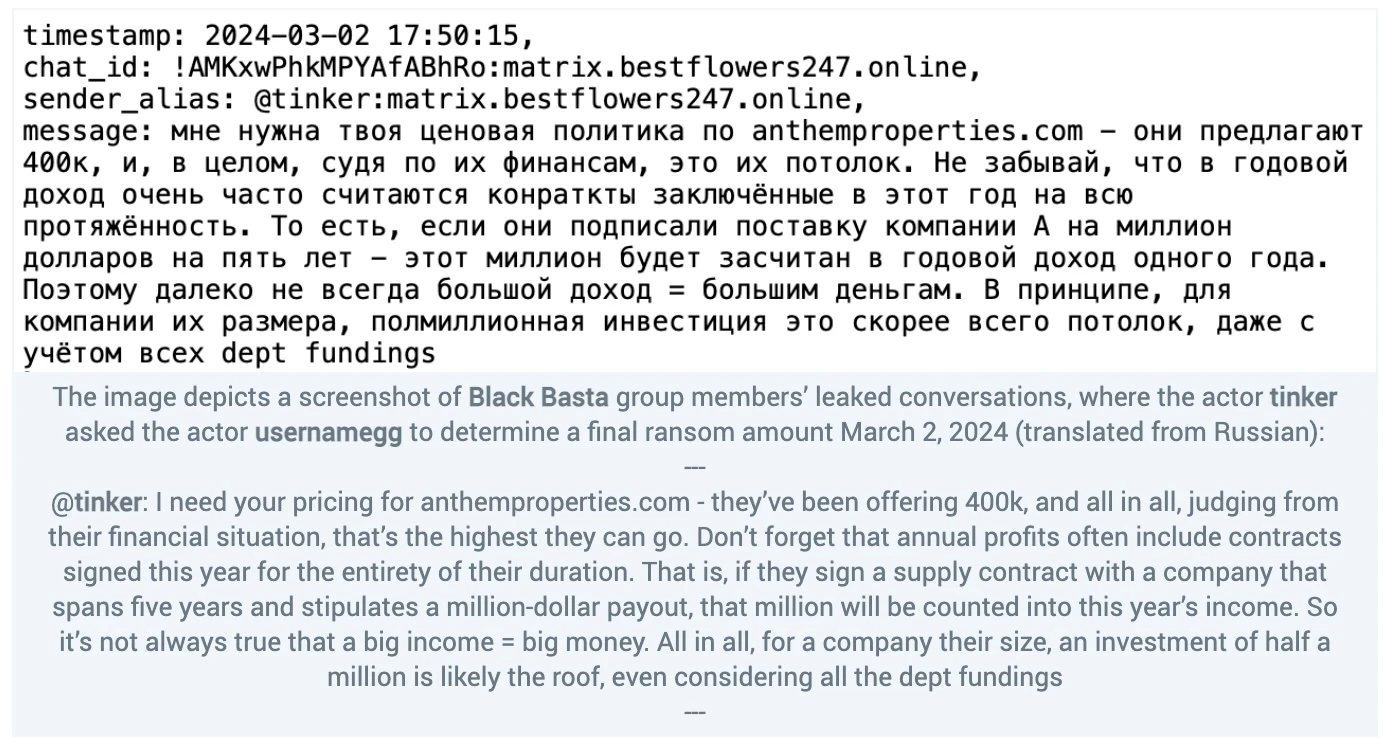
The actor tramp typically handled negotiations but said the actor would get others to help if a target required “rough treatment.” The Black Basta team’s negotiation strategy included manipulating financial data extracted from the impacted companies. The leaked conversations reveal tinker would analyze the financial data and evaluate a victim’s situation before direct negotiations. This in theory allowed tinker and tramp to set a ransom amount that met the victim’s ability to pay and increased the chance of successful extortion. The chats reveal tramp and tinker would go back and forth over the ransom amount. The actor tinker generally tended to “settle for less” than the initial amount and sought to secure a successful transaction. However, tramp preferred a more aggressive approach, setting a higher ransom amount and exerting pressure on a victim. The final decision was left to tramp. In the chat below, tinker makes a reasoned case based on both what a victim said and stolen internal financial documents the actor had analyzed.
As noted before, tramp would ask for help for more difficult victims. They were sent messages or received calls to instill fear and panic during negotiations. The actor tinker would sometimes be called on to turn the screws on a victim, as the actor had a knack for writing intimidating threats. For example, tinker provided the following text during unproductive negotiations with representatives of a national U.S. law firm. The following is an abridged version to remove offensive content and for conciseness.
1. If the data is published it is not a loss for us.
2. This is because we will only publish enough data to create a clear data breach visible on our blog. We will also put this chat there - so everyone knows how broke you are. I will also add data on your cashflow, so everyone knows that you are lying about being broke. You have this fat-ass payment for class action law suit on the way.
3. All the critical data - client cases, legal cases, lawsuit, etc - all this we will sell. You can't imagine how many cybersecurity companies have accounts on darkweb forums for this purpose.
4. We also will give a copy of the data to interested nation state parties. I am looking at China now, as well as Iran. I saw some very interesting details on intellectual property in your telecom lawsuits. I know exactly a person who will LOVE to read this.
Do you really want me to keep digging and getting more operational plans on how to monetize your data?
In April 2024, tinker wrote a script for a phone conversation for an organization that was apparently unaware of the breach or refused to communicate with the attackers. The following is an excerpt:
Hello, my name is Eric. I am calling from the BlackBasta group regarding the recent cybersecurity incident taking place in your company. Can you connect me with your management?
Our name is BlackBasta Syndicate, and we are the largest, most advanced, and most prolific organized group currently existing. We are the ultimate cyber tradecraft with a credential record of taking down the most advanced, high-profile, and defended companies one can ever imagine. You can Google us later; what you need to know now is that we are business people just like you.
We have your data and encrypted your files, but in less than an hour, we can put things back on track: if you pay for our recovery services, you get a decryptor, the data will be deleted from all of our systems and returned to you, and we will give you a security report explaining how we got you.
If the targets remained unresponsive, tinker would conduct additional open source research to obtain contact information for the company’s senior staff. The Black Basta group would also provide a file tree of the exfiltrated data to the victims during negotiations, which the actors called a “listing.” This allegedly allowed victims to see a full list of stolen files and select those they wanted to receive as proof of a compromise. The actor tinker was responsible for delivering file trees to victims and finding the files they requested.
The Black Basta group ran an initial access team that was designed to deliver fresh supplies of compromised organizations to its in-house penetration team for further exploitation. To gain access, the team used different phishing and social-engineering schemes. These techniques involved luring employees to phishing pages where they may divulge credentials. They would also call employees at organizations pretending to be from the information technology (IT) department, tricking them into installing remote monitoring and management (RMM) software that was eventually leveraged to deploy ransomware.
The actor tinker played a key role in these phishing and calling schemes. On April 20, 2024, tramp tasked tinker with writing a phishing email for a campaign that would target users of FortiClient virtual private network (VPN) software. The phishing email would contain a fake security notice with a malicious link to a fake corporate login portal. The actor tinker claimed to have previous experience conducting phishing campaigns that targeted CrowdStrike endpoint detection and response (EDR) software users in mid-2022 while working with Conti. On April 22, 2024, two days after the initial tramp conversation, tinker provided the draft text.
In another example, tinker created call scripts for the initial access operations team. In one example, on May 23, 2024, tramp asked tinker to work on a scheme using Microsoft Teams’ cloud-based phone system to target corporate employees. Callers would use compromised Microsoft 365 accounts within an organization to directly call employees.
The actor could work fast. In under an hour, tinker wrote the phishing scenario. The scenario revolved around a fictitious IT department employee named Owen. Owen advises the victim that the company is experiencing a massive spam attack that delivers malware through phishing emails. Owen then guides the victim to install AnyDesk, an RMM application, which will be used to “secure your system.” After the RMM software was installed, the caller would contact one of Black Basta’s penetration testers, who would then move to secure persistent access to the system and domain.
The leaked messages reveal some payments tinker received from tramp, as bitcoin wallet addresses linked to tinker appear in the chats.
— On Dec. 20, 2023, one of tinker’s wallets received 0.18682 bitcoin (about US $16,800) but the purpose was not provided in the conversations.
— On Feb. 12, 2024, another wallet received 0.37598406 bitcoin (about US $33,800), which possibly was a share of ransom payments from attacks against two entities.
— On June 3, 2024, an actor transferred 0.56268274 bitcoin (about US $50,800) from two wallets to one of tinker’s wallet addresses.
— On June 10, 2024, another wallet received 0.04568111 bitcoin (about US $4,100), which allegedly was a ransom payment share from the attack against the wilsonco.com entity.
The leaked messages also reveal tramp pledged to provide a 1% commission to tinker from the ransom payment allegedly received from two organizations. However, the wallet address tinker provided for the transfer did not reveal any transactions at the time of this report.
The conversations between tinker and tramp ended June 6, 2024, when tinker claimed to have serious trouble with tax authorities. The actor allegedly was accused of tax evasion, which was a result of tinker’s failure to declare income from a previous collaboration with the Conti ransomware group. It is unknown what group tinker may be working for now. The threat actor’s real-life identity is also a mystery. This person’s skills and experience, however, would be in demand in the ransomware ecosystem. Intel 471 closely follows ransomware group activity, their tactics, techniques and procedures (TTPs) and malware. For more information, contact us.