
Pro-Russian hacktivism: Shifting alliances, new groups and risks
Pro-Russian hacktivism campaigns continued to be directed at countries and entities supporting Ukraine. Here's a briefing about new hacktivist groups and the risks the groups pose.

Both of these things are true: Big data is big business, and cybercriminals love money. So it shouldn’t be a surprise that these two ideas have blended together in some corners of the cybercrime underground.
Through Intel 471’s observation and analysis of open source information and behavior on multiple closed forums, we found actors adopting the use of legitimate big data technology for cybercrime and monetizing the data they obtain on the Chinese-language underground.
The behavior we have analyzed points to a cycle that involves several different layers of cybercriminals, the use of insider information, and unwitting victims in order to earn ill-gotten gains. The schemes themselves proliferate partly due to China’s desire to be a global epicenter in big data analytics, especially as it pushes to become synonymous with new technology sectors like the Internet of Things (IoT). With China injecting big data into every economic sector, the environment has become ripe for criminals to create and execute schemes that hide in the noise brought on by the amount of data at hand.
As big data becomes a key cog in Chinese industry, the management, regulation, and governance around data has become a growing challenge for the country. Like much of the industrialized economies in the world, China’s big data sector is worth hundreds of billions of dollars.
A 2019 report compiled by the China Industrial Control Systems Cyber Emergency Response Team (CICS-CERT) that examined more than 3,000 big data-related companies found that the industry was worth more than 800 billion yuan (about US $122 billion) in 2019. By the end of 2020, the report projected the industry’s worth to exceed 1 trillion yuan (about US $156 billion). Another report published earlier this year by a Chinese think tank found big data practices were well integrated with the communications, finance, internet and security industries. Increasingly, it is also becoming a key part of business in sectors such as energy, industry and transportation.
That growth has not been paired with oversight. We observed several problems documented in open source articles that reported the increased difficulty of regulating and governing big data. The lines between private and public data are not clearly defined, while security risks in data collection, storage and sharing add to the challenges from a security perspective. The correct usage and protection of personal information in China is largely dependent on the companies themselves.
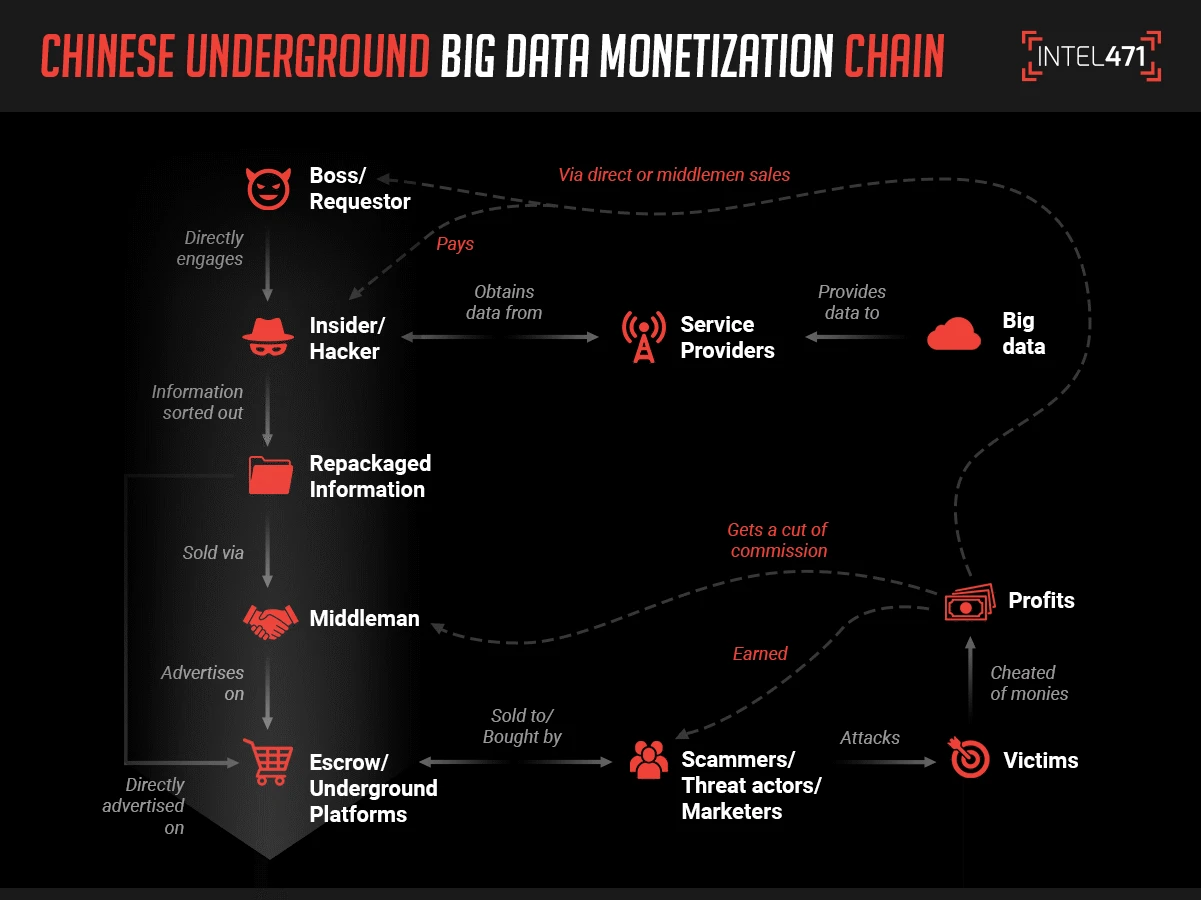
We have observed the a data underground monetization chain within the Chinese-language underground consisting of the following groups or individuals with a clear division of labor, responsibilities and a delineated chain of command that includes:
The graphic below shows how this chain tends to progress:
Intel 471 has observed numerous listings on forums popular in the Chinese cybercrime underground, including:
Chinese law enforcement has tried in recent years to hold companies accountable for how they handle. In 2019, seemingly legitimate Chinese companies also were observed providing third-party data crawling services and selling the data collected from unknown victims to reap a profit in addition to being exploited by underground threat actors. Our research identified an article discussing the circumstances surrounding the arrests of the following individuals and entities:
According to the Chinese state broadcaster China Central Television (CCTV) on its annual name-and-shame television program 3.15晚会 (Eng. 3.15 Gala), another 11 companies were exposed for harassing people over the phone, marketing big-data related products and services that are actually against Chinese privacy laws, and other violations of user privacy. Although the companies named were not large in operational scale, they were linked to a bigger group of well-known companies.
Chinese authorities reportedly adopted measures to crack down on the illegal big data trade and tighten regulations governing personal data and privacy. A series of regulatory measures regarding internet privacy protection and the security of personal information reportedly was introduced by the Cyberspace Administration of China in addition to the large-scale crackdown.
Nations that are highly digitized have struggled with privacy over the last decade. We’ve seen laws like GDPR, CCPA, and PDPA put in place to help citizens exercise some control over the information they generate on the internet. However, if more scenarios like China’s underground big data trade are replicated as other countries develop data-reliant economies, regulations and law enforcement are going to face an uphill battle in stopping data trading schemes. The prevalence of these schemes show the importance of securing the data businesses generate on the same levels as the services that keep business running on a day-to-day basis.

Pro-Russian hacktivism campaigns continued to be directed at countries and entities supporting Ukraine. Here's a briefing about new hacktivist groups and the risks the groups pose.

NATO's annual summit comes as member countries face a rapidly changing global security dynamic, with cyber playing a significant role.

Underground call center services are aiding threat actors in delivering malware through callback phishing and negotiating ransoms. Here's a briefing about different attack scenarios and tips for defense.
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.