
Pro-Russian hacktivism: Shifting alliances, new groups and risks
Pro-Russian hacktivism campaigns continued to be directed at countries and entities supporting Ukraine. Here's a briefing about new hacktivist groups and the risks the groups pose.

Most cybercriminal schemes don’t happen all at once. There are multiple parts to an attack, with each part needing some support from infrastructure to succeed. Take for instance, Hancitor, a very popular piece of malware which sets the stage for cybercriminals to launch a variety of different attacks. It’s been used to allow drops of banking trojans, information stealers, and other types of malware. In use since 2014, it’s delivered via spam that contains a link someone must visit. That link, if clicked on, leads to a malicious document that drops Hancitor on a victim’s machine.
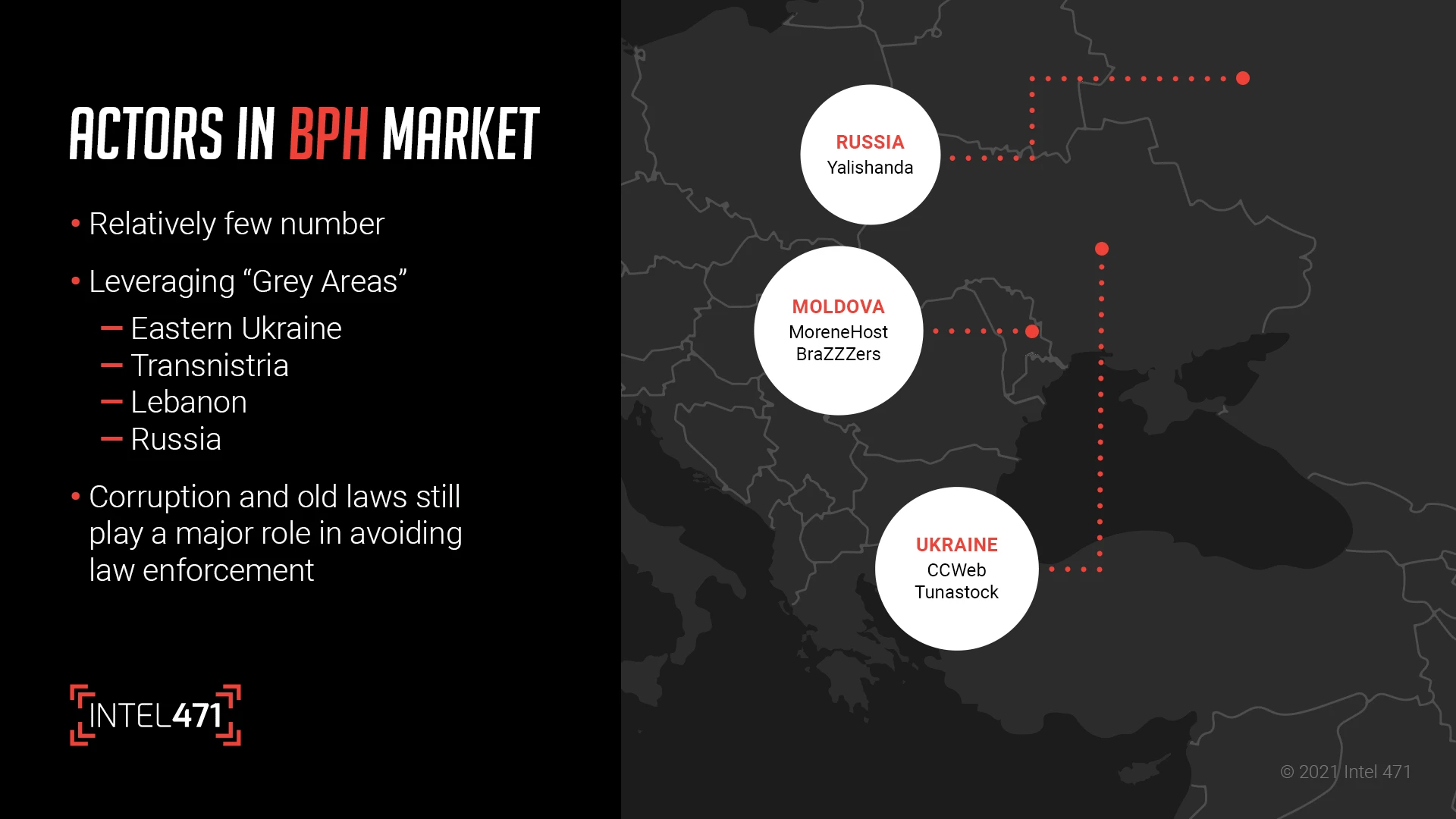
From 2018 to December 2020, that link pointed to an IP address that is part of a fast-flux offering from Yalishanda, a notorious bulletproof hosting provider in the cybercriminal marketplace. The offering, buried in the noise of top-tier cloud service providers — like Alibaba, Google Cloud and Selectel, among others — allowed not only Hancitor to thrive, but every effort associated with the array of secondary malware that can be used.
Hancitor is just one of many examples that shows how bulletproof hosting is the key hidden enabler for a significant portion of the cybercrime underground. While it’s full of all types who make money through illicit products and nefarious services, there is a subset of actors that are profiting from the infrastructure that supports these schemes. BPH providers advertise specific services based on their own unique setups, but will often provide support that goes beyond what they tout on the underground forums, allowing them a means of income while remaining a level away from the direct criminal actions.
While bulletproof hosting is often difficult to quantify and to eliminate, taking these services down or limiting their efficacy can have an immense impact. Intel 471 has seen this whenever there is a takedown: actors are abuzz with complaints, the targeted services go into damage control, and competing services start offering specials while also offering condolences to their competition. Also, if a security operation knew what to look for with regards to BPH services, they would have been protected from the above Hanictor example, as well as any subsequent secondary payloads.
The following is a list of some of the BPH providers that are firmly entrenched in the cybercrime underground and how they give support to other cybercriminal enterprises. By recognizing their behaviors, security teams can begin to take measures to figure out who the actors are, how they operate and what their infrastructure looks like. By doing so, organizations can begin to uncover ways to proactively counter maliciously-used infrastructure before criminals have a chance to launch their attacks.
In operation since 2016, MoreneHost has been among the most prolific bulletproof hosting providers in the cybercriminal underground. Over the past five years, the actor has operated services under several different names, including IronHost, Perfect Quality Hosting and IntersectHost.
MoreneHost has operated a fast-flux service since 2018, leveraging internet service providers based in France, Russia and Ukraine. As the service grew, the operator also added IPs from Moldova and The Netherlands. The operation itself is believed to be run from Transnistria.
Since being stood up, the service has provided hosting for a number of illegal resources, including:
At one point over the past five years, MoreneHost’s services were hosting instances of a variant of the ZeuS banking trojan known as Panda Banker. Additionally, Intel 471 has found an actor using a custom PowerShell script being hosted by IPs known to be linked to MoreneHost that could exfiltrate data about a compromised system and run commands from a remote command and control (C2) server. This script was used in a larger effort to deploy DarkSide ransomware.
While MoreneHost has been a known entity on the cybercrime underground, the operator has changed brands over the past few years partly due to a fluctuating reputation. It's thought that the actor was part of another popular BPH service as far back as 2009 under the now-defunct brand DonServers. An account on one prominent underground forum associated with the service went dark for months in the second half of 2019, after there were several complaints filed regarding the quality of the actor’s service. He was ultimately banned in January 2020 after refusing to offer services to a person who paid for them. He resurfaced in 2020, launching a service under a similar name after a previous owner was arrested by Russian law enforcement.
Another actor that has been around for more than five years, Tunastock has been a very active member on both low-level and prolific underground forums. While providing similar services to other providers on this list, Tunastock made a name for himself by providing SSH tunnels and SOCKS proxies, which allow criminals to hide their true origin and exfiltrate data via encrypted connections.
Within the last year, one actor alleged that he used Tunastock SSH tunnels to take data from a popular web analytics company and a Chinese software company, as well as gain root access to several databases and development platforms belonging to a social media network that sees 10 million visitors a month. Additionally, another actor looking to use malware targeting internet-of-things devices also claimed to be using Tunastock’s BPH services.
Intel 471 has observed some indication that Tunastock may have been partners with Mykhailo Rytikov, also known as Whost, before law enforcement agencies dismantled his data center that held 150 servers and equipment that was used for a variety of schemes, including DDoS attacks, spam campaigns, and pornography. It’s worth noting that Rytikov is considered by many to be an “old wolf” of the cybercriminal underground with a presence going back to the Russian Business Network (RBN) days where he provided a BPH service under the moniker “Abdallah.” While the full scope of the partnership is unclear, Intel 471 observed Tunastock using Whost’s infrastructure to host Tunastock’s Jabber server, which suggests a degree of trust and cooperation between the two providers at some point.
A relative newcomer to the underground, bpnode has been actively promoting their bulletproof hosting services on forums used by criminals since May 2020. The actor primarily sticks to low and mid-level hacker forums or his own Telegram channel, which at one time had over 100 members.
Among the services offered by this actor are:
Intel 471 also found this infrastructure hosting phishing pages targeting users of well-known Western banks, financial services, e-commerce, retail technology, and telecom companies.
Additionally, Intel 471 found IP addresses hosting AZORult and Amadey malware loader distribution campaigns.
First surfacing in 2018, BraZZZerS has become one of the most relied-upon BPH providers currently on the cybercrime underground. The actor’s fast-flux infrastructure leverages a number of front-end proxies and servers as nodes; with each client provided a unique IP address.
At one point thought to be either an associate of or partner with MoreneHost, BraZZZerS has since gone to build offerings that can guard services with tens of thousands of different IP addresses. The schemes supported by BraZZZerS include the following:
Additionally, the actor has become very adept at reloading the IP and web addresses in their catalog. Due to the way fast-flux networks operate, the domain-name-to-IP-address resolution being used by BPH providers is altered at a very high frequency. Over a three-month period in 2020, BraZZZerS utilized over 140 unique IP addresses and over 1,100 domain names for his customers’ use. This process has carried out multiple times since the service has grown in popularity.
In operation for more than a decade, ccweb is a veteran of the cybercrime underground. He provides a wide range of bulletproof services including virtual private servers (VPS), virtual dedicated servers (VDS), dedicated servers, domain name registration and a double fast-flux network which provides a high level of protection to customers. His double fast-flux hosting network, commonly referred to as Fluxxy by security researchers, is a unique offering in the cybercrime underground that serves as his primary offering. The service is supported by a wide array of “child” and “parent” name servers. The “child” name servers are proxy bots stationed in a wide range of countries, and the “parent” name servers consist of VPSs hosted in Africa, Asia or the Middle East.
Over the past decade, the following is among the malware that has been hosted on ccweb’s infrastructure:
Over the course of the past year, ccweb has averaged 180 IP unique addresses and 40 unique domain names per month for customers to use.
Known to be active on the underground since 2007, this actor has made a name for himself as the preeminent BPH provider for cybercriminals since 2015. A Russian native that has operated out of both Russia and China, Yalishanda is constantly updating his front-end proxies to allow his customers to use his services for a whole host of scams. If you can think of an action that a cybercriminal would benefit from, Yalishanda’s infrastructure has likely hosted it at some time: DDoS, spam campaigns, phishing pages, and a catalog of ransomware variants.
This is a sampling of the malware hosted on Yalishanda’s infrastructure, either currently or at one point, since 2015:
Similar to our ransomware list, this entry is not a comprehensive directory of BPH providers. There are many more that operate in the ecosystem, allowing cybercriminals to launch an attack while hiding from consequences. In order for enterprises to be aware how cybercriminals target their organization, they must be aware of how the cybercrime underground functions. Once that understanding is reached, the security community can focus on blocking this infrastructure from its networks and law enforcement can focus on eliminating the foundation by which the cybercriminal underground operates on top of.

Pro-Russian hacktivism campaigns continued to be directed at countries and entities supporting Ukraine. Here's a briefing about new hacktivist groups and the risks the groups pose.

NATO's annual summit comes as member countries face a rapidly changing global security dynamic, with cyber playing a significant role.

Underground call center services are aiding threat actors in delivering malware through callback phishing and negotiating ransoms. Here's a briefing about different attack scenarios and tips for defense.
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.