
Pro-Russian hacktivism: Shifting alliances, new groups and risks
Pro-Russian hacktivism campaigns continued to be directed at countries and entities supporting Ukraine. Here's a briefing about new hacktivist groups and the risks the groups pose.

By the Intel 471 Intelligence Analysis team.
Here at Intel 471 we spend a fair amount of time tracking malicious infrastructure providers. In the world of cybercrime the malicious infrastructure provider, or Bulletproof Hoster (BPH) as they are called in the underground marketplace, is a core enabling service that often gets little attention from threat intelligence analysts. It’s difficult to quantify their impact as it’s often spread over the activities of many different clients that are conducting activities that range from low-level phishing to more sophisticated intrusions. Sure, IP addresses and domains associated with badness get pushed over to the NOC/SOC, SIEM or endpoints to protect the enterprise, but few are digging beyond the initial incident and indicators then working up the chain to prefixes, Autonomous System Numbers (ASN) or even the companies behind them.
As you divert your attention to the malicious infrastructure provider and move up this chain, you’re dealing with aspects of the bad guy’s business model that are more costly to put in place and thus change less frequently. You’re also allowing for opportunities to identify, track and proactively block clusters of infrastructure that, while not yet used for malicious activity, have been set aside for such badness. In this blog we’ll start with some infrastructure suspected to be in use by TA505 and make the case for blocking the entire associated prefix as well as using BGP announcements to monitor for future indications of infrastructure being put in place.
Through the course of our research we’ve identified a couple of IPs addresses suspected to have been used in secondary activity by TA505, so if you’re seeing these then it means you’ve potentially got some big problems.
176.121.14.175
176.121.14.238
These are a bit more significant to TA505 operations than Get2 Loader malware infrastructure, which are used early on as part of the initial infection. Get2 Loader is widely thought to be the loader operated by TA505 early on in their intrusions. This infrastructure will typically see more frequent turnover given its position in the chain, but the same exercise can be done with those domains & IPs as well…and it’s worth doing.
When looking at an IP address there are few red flags that should get your attention. It’s certainly not a perfect science, but they do offer indications you may be dealing with BPH infrastructure set aside to support malicious activity.
To give a quick and simple example we’ll start with the two IPs mentioned above as being associated with TA505 activity. The first thing we want to understand is the smallest prefix announcement and routing history associated with the IP address. That’s pretty easy using RIPE’s free tool RIPEStat. The key takeaways from the screens below are that both IPs have been part of 176.121.14.0/24 since mid-2018 and it is currently announced by AS210138. Also, this prefix provides a fairly small number of IP addresses — 256 to be exact.
https://stat.ripe.net/widget/routing-history#w.resource=176.121.14.175
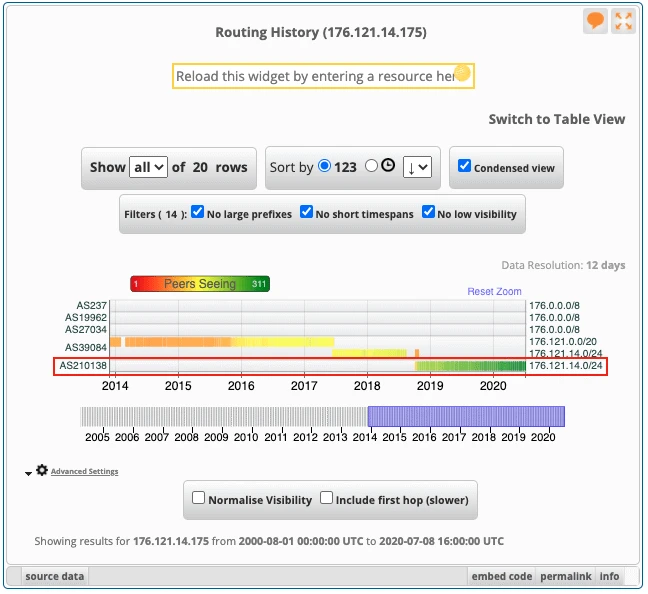
We can also use RIPEStat to understand the routing history for AS210138. This will provide you information related to what other prefixes have been and are being announced under a particular Autonomous System (AS). What we can see is that AS210138 has only announced the subject /24 IPv4 prefix since October 2019 and the IPv6 /48 since in April 2020. If you were confident an ASN was controlled by a malicious infrastructure provider you could make the case for blocking any prefixes associated with it currently and in the future.
https://stat.ripe.net/widget/routing-history#w.resource=AS210138
We can look further into the ASN, the parent organization, and more using the RIPE database and other tools, but that’s beyond the scope of this blog. We’ll stick to three RIPE objects (person, organization and ASN) that provide some pretty decent insight into the AS and those that control it.
https://apps.db.ripe.net/db-web-ui/lookup?source=ripe&key=AS210138&type=aut-num
https://apps.db.ripe.net/db-web-ui/lookup?source=ripe&key=ORG-FL235-RIPE&type=organisation
https://apps.db.ripe.net/db-web-ui/lookup?source=RIPE&type=person&key=NS7363-RIPE
The information gleaned from the RIPE DB and from RIPEStat is somewhat more reliable than domain WHOIS as it can’t all simply contain dummy data and some of it is related to BGP, which needs to be legitimate if you’re going to play on the internet. To summarize some of the info we’ve pulled together:
Next, we consider the question of whether or not this particular organization is catering its services to cybercriminals directly in the underground marketplace. A quick look across a number of forums will show that Flowspec is operating in plain sight and clearly offering bulletproof hosting services. It’s not always this easy to answer this question, however.
We’ve taken an abbreviated look at Flowspec’s setup, but what we can conclude is that TA505 are likely active in the underground marketplace and using the BPH services of Flowspec. It’s a safe bet to also conclude that nothing good is coming out of Flowspec’s /24 and it’s more or less set aside for nefarious activity. TA505, a somewhat sophisticated adversary, are just one of a number of clients so to block that /24 will also help defend against any other badness originating from Flowspec.
Course of action (COA) analysis must take into account your organization’s capabilities, but below are a number of simple COAs that might make this sort of research and analysis actionable for your organization.
Join us on July 23rd, 2020 for our TA505 Deep Dive webinar that will cover the group’s history including TTPs.
Register at: https://us02web.zoom.us/webinar/register/WN_Z_YvCOXHRweL6vW3EoqO2Q

Pro-Russian hacktivism campaigns continued to be directed at countries and entities supporting Ukraine. Here's a briefing about new hacktivist groups and the risks the groups pose.

NATO's annual summit comes as member countries face a rapidly changing global security dynamic, with cyber playing a significant role.

Underground call center services are aiding threat actors in delivering malware through callback phishing and negotiating ransoms. Here's a briefing about different attack scenarios and tips for defense.
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.