Supercharge your security with intelligence-driven threat hunting, and immediately upskill teams into advanced threat hunters to defend against cyber threats.

Intel 471’s intelligence-driven threat hunting helps you proactively seek out threats that have snuck past defenses and lurk undetected within networks. We help reduce the time between intrusion and discovery, and mitigate the risk of impact from a cyber attack, including costs that impact the bottom line, brand, and reputation—even public safety. Intel 471 transforms your teams into skilled threat hunters, and helps them conduct structured hunts, unstructured hunts, and situational hunts.
Intel 471’s threat hunt and hunt management solution, HUNTER, puts expertly-crafted behavioral threat hunts at your team’s fingertips. HUNTER’s growing library of behavioral hunt packages amplifies your threat hunting program with advanced hunt queries for major security platforms. Each hunt has been validated by our experts to identify advanced threat behaviors and help your team stop adversaries in their tracks.
The HUNTER Hunt Management Module provides Intel 471’s industry-leading methodology for managing team hunts and measuring hunt performance metrics. It helps overcome the challenge of demonstrating the return on investment of proactive threat hunting. The module drives rigorous, repeatable, and consistent hunt processes that help teams identify and close gaps in security controls and logging.
Intel 471’s HUMINT-driven adversary and malware intelligence fuels HUNTER, giving your threat hunting teams hundreds of pre-validated and contextualized hunt queries written by Intel 471’s world class threat hunters. Our hunt packages help your threat hunters proactively seek out unknown and undetected threats inside your environment, reducing threat actor “dwell time” to mitigate the cost of suffering a major security breach.
HUNTER powers the growing demand for in-house threat hunting programs and helps overcome critical skills shortages. With threat actors routinely using “Living Off The Land” (LOTL) tactics to evade detection, in-house threat hunting programs have become a strategic priority for most CISOs. HUNTER makes it easier and far more affordable for teams to perform behavioral threat hunts targeting the latest tactics, techniques and procedures (TTPs) of top-tier threat actors. As depicted below, TTPs are much harder to change than Indicators Of Compromise (IOCs). However, focusing on evolving TTPs is much more effective than hunting for ephemeral IOCs.
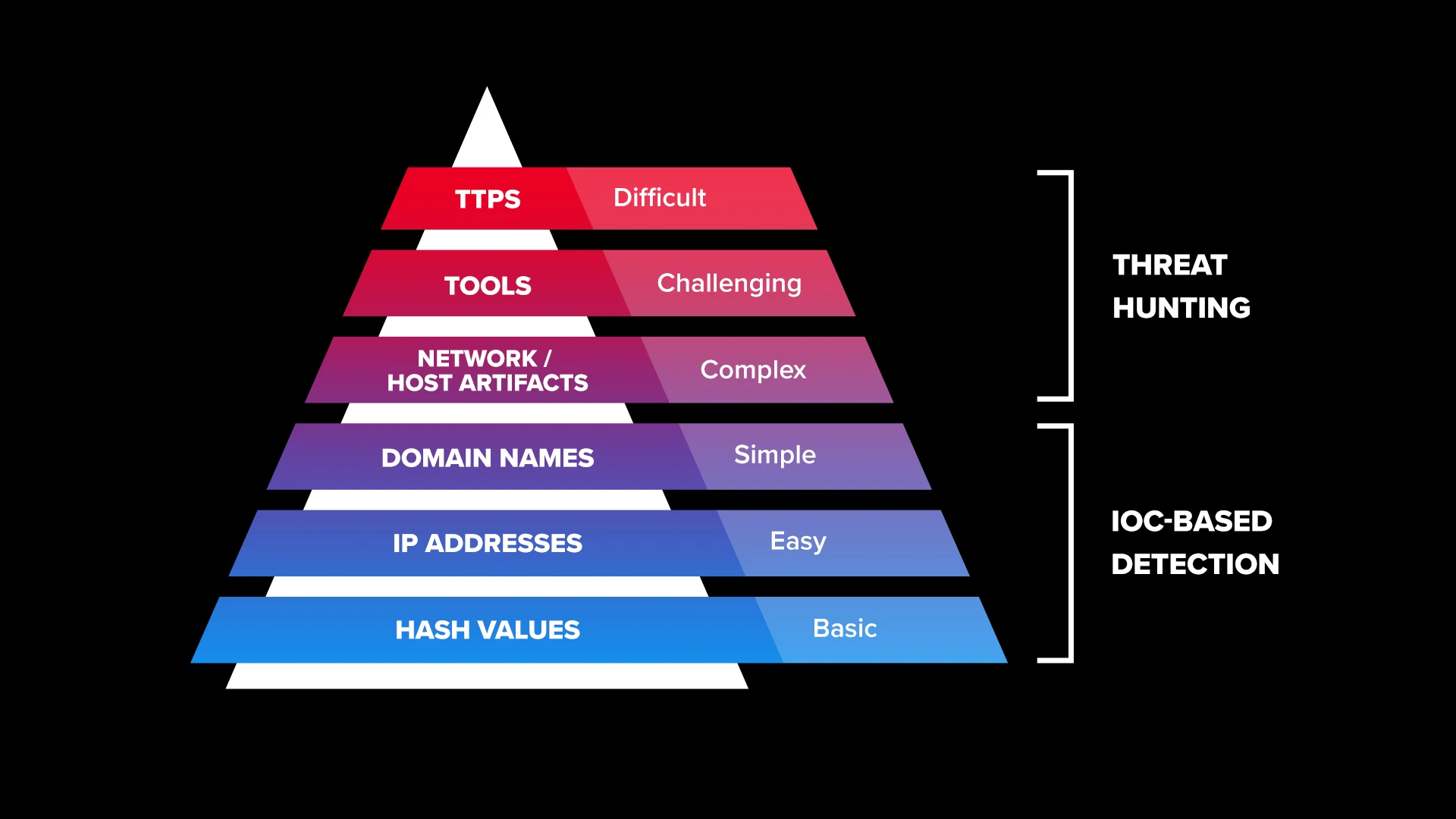
HUNTER hunt packages do the heavy lifting of research and hypothesis-development in the threat hunting cycle, allowing your team to immediately search for undetected threats, ensuring every minute spent on a hunt is beneficial, measurable and effective.
Each hunt package offers emulation and validation files to help your hunters simulate an attacker’s behavior in a safe and controlled environment to improve targeted detection and prevention mechanisms, fast-track incident response and create new adversary insights specific to your environment. Read more about The Business Value of Threat Hunting to understand why integrating our behavioral threat hunting content into your threat hunting program solves hiring challenges and can transform your hunt strategy.
Reduce dwell time for previously undetected threats
Enrich threat intelligence with adversary insights specific to your environment
Identify gaps in MITRE ATT&CK methods covered by hunts
Convert hunt findings into new detections for EDRs and SIEMs
Find visibility gaps in endpoint and logging configurations
Discover and prioritize vulnerabilities and misconfigurations for remediation
Bring Your Own Hunt content to leverage the HUNTER methodology
Guided Threat Hunts help analysts overcome large data sets
Identify and mitigate advanced threats during all phases of the attack lifecycle with intelligence-driven threat hunting.
Use Case
Operationalize threat hunting content on your security platforms, and upskill teams to detect, investigate and mitigate advanced threats.
Use Case
Engineered to meet hunt team demands, streamline threat hunting, and provide comprehensive metrics, analytics and real-time ROI to demonstrate threat hunt program effectiveness.
Use Case
Intelligence-driven behavioral threat hunting is a powerful method for identifying security control gaps and prioritizing their remediation based on current threats to the organization.
Cyber Threat Hunting from Intel 471: Neutralize Threats
Intel 471 helps your hunters stay knowledgeable and prepared to identify and disrupt advanced persistent threats before they strike with up-to-the-minute intelligence and unparalleled insights into cyber threats.
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.