PATCHING IN THE DARK: EXPLOITS INCREASING, ATTACK SURFACE EXPANDING
The exploitation of vulnerabilities is a root cause of damaging data breaches, intrusions, and cyber attacks. In fact, Verizon’s Data Breach Investigations Report 2025 noted that vulnerability exploitation was the initial access vector in 20% of breaches.
Security teams are under immense pressure as they struggle to balance the volume of patches they must apply against resourcing constraints. When each vulnerability poses a different risk to each organization, there is a danger that critical patches may be overlooked, presenting adversaries with targets across the attack surface.
These attack surfaces are also expanding at an unprecedented rate, complicating the issue. Cloud adoption, third-party software-as-a-service (SaaS), and remote working increasingly result in patch management being outside of an organization’s control and unpatched assets being out of sight.
Patch prioritization demands real-time risk insight and continuous visibility of assets. Without this, critical gaps remain exposed to cyber threat actors while resources are wasted elsewhere.
INTEL 471’S INTELLIGENCE-DRIVEN PATCH PRIORITIZATION
Purposeful patch prioritization demands best-in-class intelligence. Intel 471’s cyber threat intelligence ensures you can focus on the vulnerabilities that pose the most risk to your organization. We track the full threat lifecycle of vulnerabilities using both open sources and the dark web to monitor threat actors expressing interest, weaponization, sharing proof-of-concept and more. By illuminating the precursors to exploitation, we empower you to prioritize patching based on real-world actions, not theoretical risk, so you can effectively protect your assets. Intel 471 also provides continuous scans of your external attack surface, to pinpoint and contextualize vulnerable assets to address.
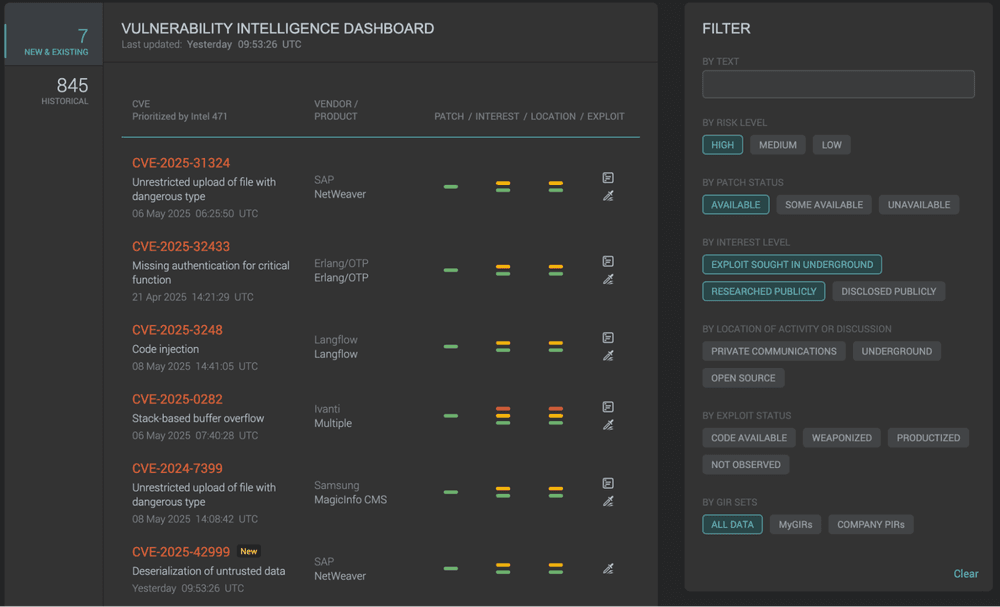
ALIGN YOUR PATCHING WITH VULNERABILITY LIFECYCLES
Key features and benefits offered by Intel 471 include:
Vulnerability lifecycle tracking
Use our dashboard to track the lifecycle of vulnerabilities, from initial disclosure to exploit productization. Tracking precursors to exploitation offers an analyst-driven assessment of priority vulnerabilities beyond keyword hits, and ensures a proactive approach to vulnerability management as your organization can discern what threats are on the horizon versus which are at your door and prioritize accordingly.
Continuous, contextualized monitoring
We track known and emerging vulnerabilities through open sources, such as vendor reports and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) catalog, and the dark web, using human intelligence (HUMINT) to gain access to covert spaces. We monitor the discussion and weaponization of CVEs, exploit offers, customer interest levels and more to build a full picture of the risk associated with each vulnerability and alert you as threat levels change.
Attack surface intelligence
To prioritize patching, you must know what is exposed. By continuously mapping your internet-facing assets, our Exposure Intelligence domain uncovers elements such as public facing servers, exposed cloud assets, and outdated SSL certificates; and links them to CVEs, known breaches, and the tactics, techniques, and procedures (TTPs) of threat actors. Use this context to power fully informed patch prioritization.
Integration for operationalization
Seamlessly integrate our intelligence into your SEIMs, TIPs, and other security tooling systems. Ensure data is connected to your asset management and remediation workflows to reduce response time and keep resources focused on the most critical of tasks.
Learn more about how Intel 471 can help with patch prioritization




