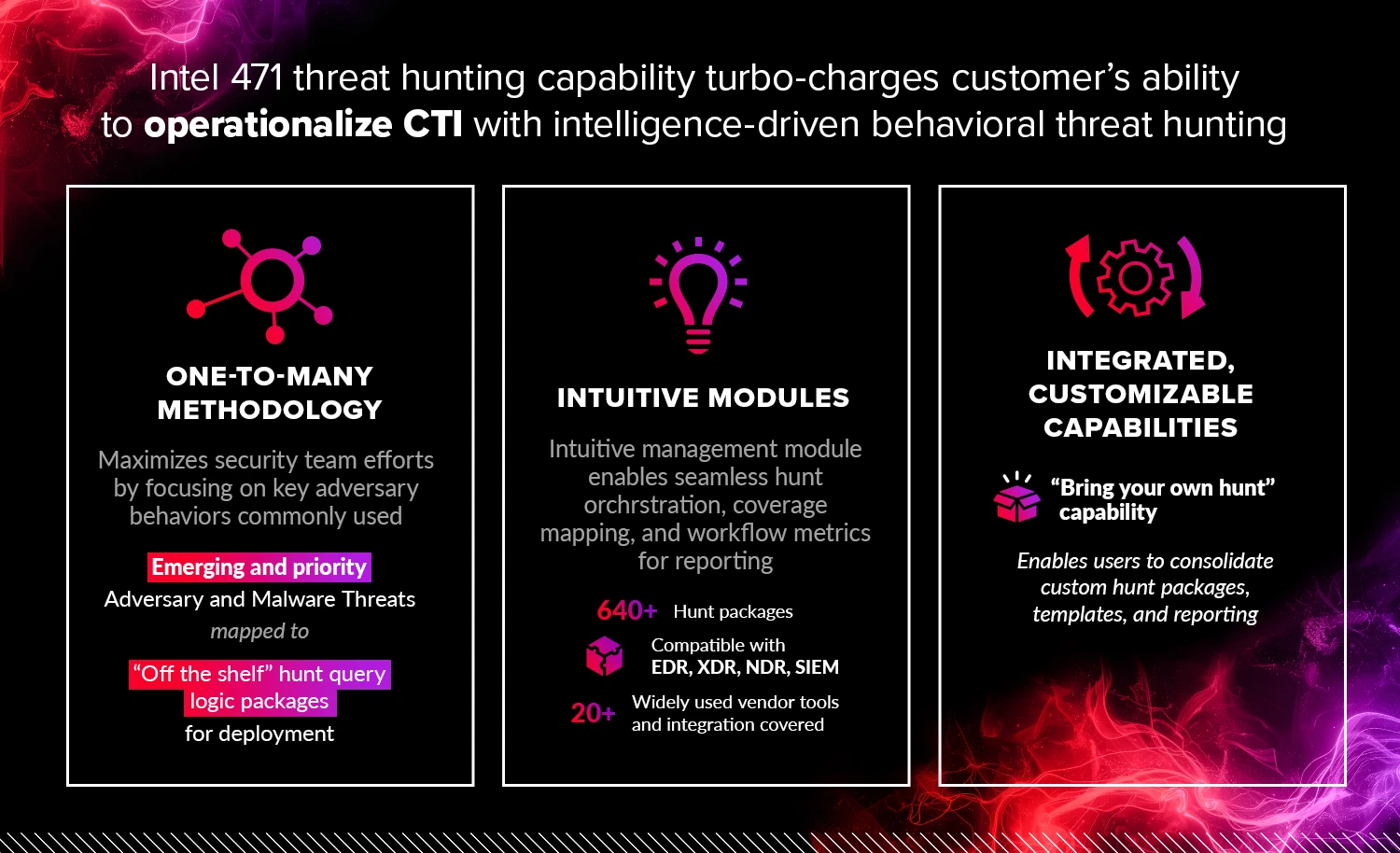
Scale and automate your behavioral threat hunting operations with consistent, rigorous, and repeatable processes.

As teams grow, they need tooling to perform consistent and repeatable processes that improve structured threat hunting methodology, which helps hunt teams stay ahead of undetected threats and evolving adversary behaviors.
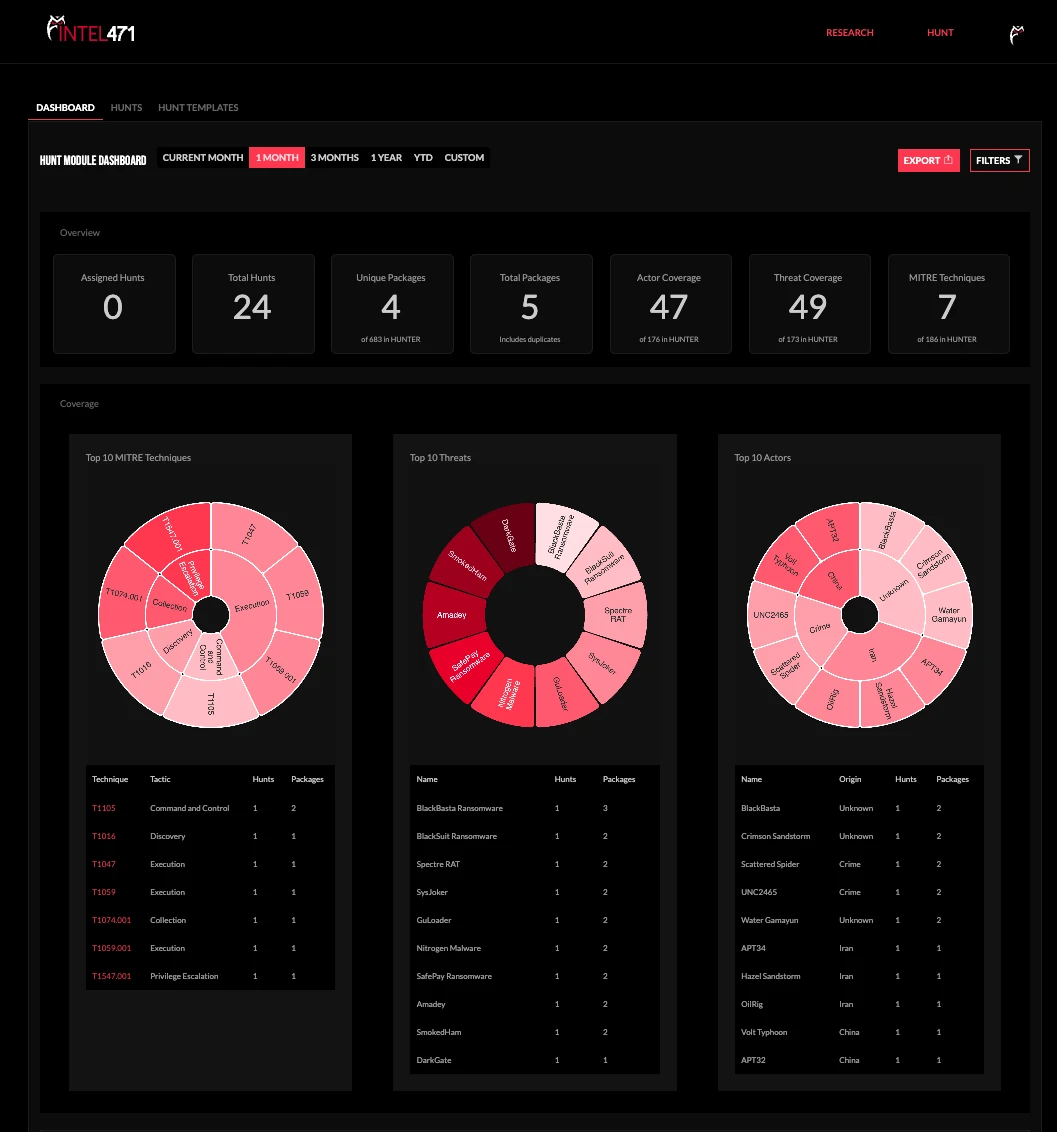
The Hunt Management Module for the HUNTER solution makes this easy as a purpose-built centralized hunt management tool for tracking and measuring key hunt performance metrics, coordinating collaborative hunts, managing hunt queries, and reporting. The tool’s interactive dashboard provides continual MITRE ATT&CK technique gap analysis, enabling teams to quickly pivot to relevant behavioral hunt packages and evaluate threat coverage.
With built-in intuitive tactical and strategic reporting, the Hunt Management Module is an essential tool for teams to monitor and demonstrate improvements to security posture and visibility in your environment.
Enable security teams to assign processes and monitor threat hunting progress. It also allows for effortless tracking, management, and coordination of ongoing threat hunting activities between incident response, security operations, and threat intelligence teams.
Provides a flexible and customizable platform for storing and managing your hunting content, including custom queries. The module also provides flexible management of key findings, evidence, and remediations.
Robust and easy-to-digest threat hunt reporting that can be easily exported and shared. The reporting capabilities allow teams to choose relevant features for strategic or tactical reporting, including: executive summaries, threat details, queries, and hunt-package details, findings, evidence, scope, remediation, and outcome.
The Hunt Management Module’s dashboard conveniently allows for managing all aspects of the threat hunting process, and offers comprehensive insights into the effectiveness of an organization’s threat hunting program.
The module’s Guided Threat Hunts feature provides expert guidance on pivoting after executing an initial hunt query, helping your team identify notable artifacts and hunt for adversary behaviors with greater speed, decisiveness, and consistency.
Maximize the value of hunt content your own hunt team builds. With BYOH, you can bring your existing hunt queries and develop new hunt content aligned with the industry-leading HUNTER methodology for hunt creation and management. It instills consistent documentation and CTI contextualization to improve hunter efficiency, collaboration, and hunt decision-making.
Create your own automations for advanced threat hunting workflows and hunt management use cases with the HUNTER API. Teams can automate the correlation and staging of hunt packages based on threat intelligence reports. Quickly search against the HUNTER API to pull all relevant hunt packages to the related report, gather technical and behavioral details, then push the query logic to your tool to stage the next steps of the hunting process.
HUNTER allows you to automate the operationalization of intelligence reports based on contextual tagging of the threats. Teams can stage all related hunt packages into a Hunt Template, execute emulation and validation packages based on the associated threats, then assign the hunt to complete the rest of the human-driven hunt process.
Save valuable analyst hours by using HUNTER’s reporting feature to complete threat hunting reports and automatically export the report and hunt information to internal tracking tools like Jira.
Deploy threat hunts faster with consistent and repeatable processes
Enable collaborative hunting across your security teams
Ease management of hunt findings and remediation
Build customized and reusable hunt templates that can be easily scheduled
Provide straightforward reporting including scope, timeline, evidence, and outcome
Experience effortless tracking, management, collaboration, and coordination of ongoing threat hunting activities between teams
Analyze insights on the effectiveness of hunts through intuitive dashboards, and demonstrate the real-time business value of your threat hunt program
Guided Threat Hunts helps your teams navigate large query data sets to identify behaviors with greater speed and consistency. A library of Pivot and Filter Queries for hundreds of HUNTER hunt packages helps your team decide the next step after receiving initial query results. Key benefits include:
Expert guidance about pivoting after executing an initial threat hunt query
Helps hunters to pivot on notable artifacts worth investigating further
Guides the user through capturing data inputs to define subsequent pivot queries
Adds Pivot Queries to HUNTER package to investigate all notable artifacts
Creates consistent, repeatable Pivot workflows within HUNTER packages
Enables standard operating procedures (SOP) for the team’s threat hunting methodology
Assist users to modify the initial query to fit their unique environment, with exclusions that reduce noise from initial results and large datasets
Decrease onboarding of new personnel, and accelerate their effectiveness to the team
The Hunt Management Module helps you get the most out of your team’s internally created custom hunt queries by letting you “Bring Your Own Hunt” (BYOH) packages to HUNTER.
This feature supports your existing and new hunt queries created by your team, allowing your team to leverage the same methodology we use for hunt content creation and hunt management on HUNTER. This helps your teams create consistent analyst documentation and mitigation notes for your in-house hunt queries that address threats unique to your environment or sector.
Signing up to the HUNTER Community Edition at no charge provides for access to dozens of these hunt packages, offering:
Sign up for your HUNTER Community Edition account now to see how it can support your threat hunting operations.
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.