Track critical and weaponized vulnerabilities and know when to act.

Monitoring the digital threat landscape for software vulnerabilities that pose a high risk to your IT environment is critical to reducing operational risk. Failing to address vulnerabilities will leave business systems wide open to data breaches, extortion attacks, and ransomware threats. Vulnerability management is one of the most challenging aspects of IT security and is growing more complex as digital transformation fuses legacy IT with cloud, AI, and mobile. Software sprawl is endemic, and with each new piece of software come vulnerabilities that need to be patched.
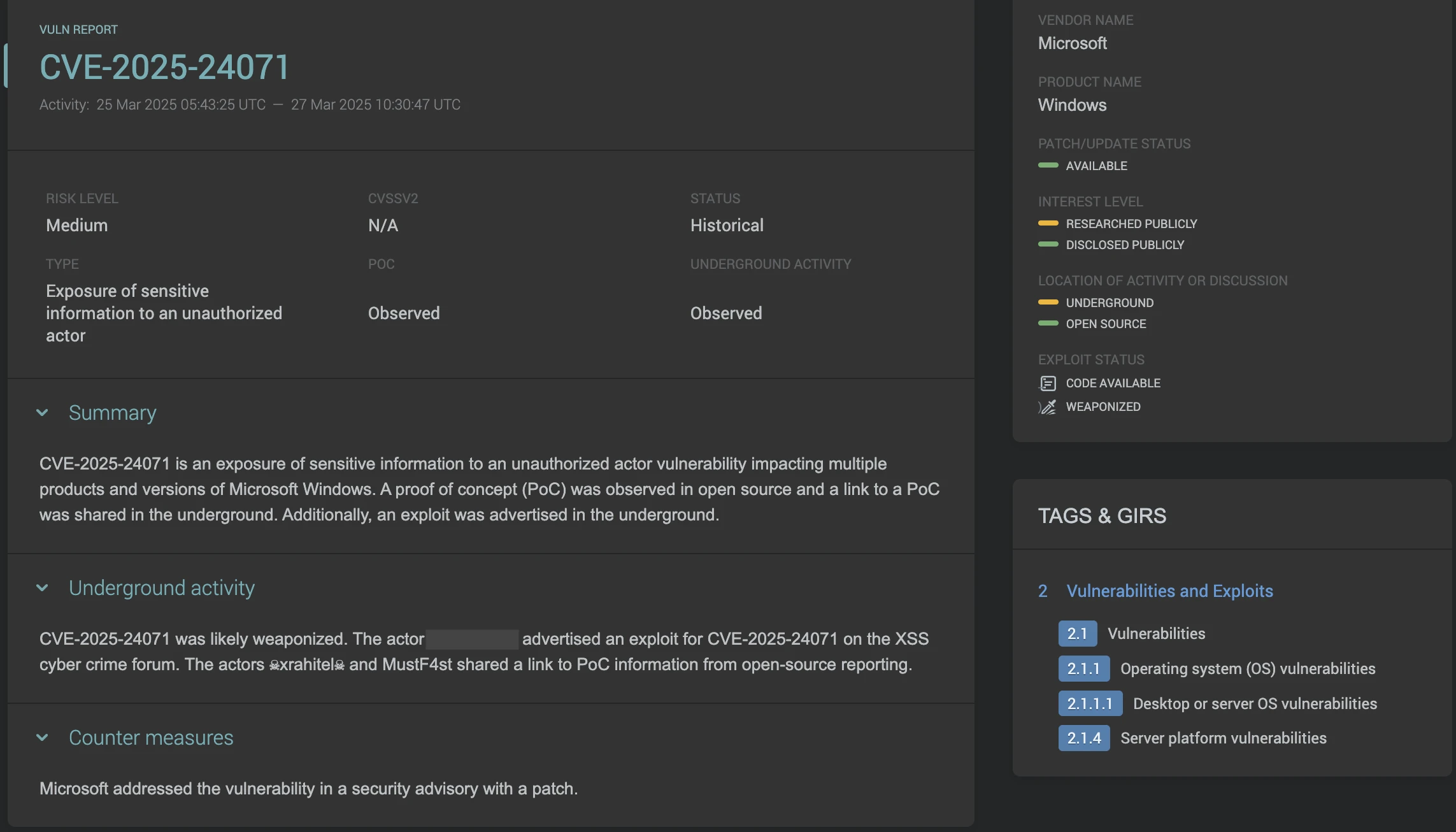
Vulnerability monitoring can help your teams make informed risk-based decisions about the vulnerabilities you should prioritize for remediation and the potential impacts on business operations from patching software.
Cyber adversaries routinely exploit misconfigurations in applications and cloud services to gain unauthorized access to data and systems. The shared responsibility model commonly used in cloud computing means customers are responsible for configurations that impact their attack surface.
Failure to apply patches will leave the software wide open to cyber attacks. Ransomware and other threat actors frequently target vulnerabilities in internet-facing applications in the days and weeks after vendors release a new security patch.
Adversaries can exploit vulnerabilities a software developer is not aware of. Nation-state and financially motivated threat actors leverage zero-day and post-disclosure n-day vulnerabilities before a patch is released to gain initial access and to elevate privileges once inside.
We leverage our presence on the cyber underground to track malware families and threat actors to provide in-depth, technical malware reports and a live feed of the latest IOCs, artifacts, and C2 information so that you can rapidly identify if a vulnerability has been exploited and work to mitigate its impact.
Continuously monitor and deliver up-to-the-minute intelligence on the latest threats to your organization so you can see your attack surface as an attacker would. Understanding how and why attackers operate, allows you to carry out preventative measures that help mitigate zero day attacks.
With Intel 471’s continuous monitoring of the vulnerability and threat landscapes, your security teams have real-time threat insights to make risk-based decisions about patching software that impacts your business operations.
Deploy Intel 471 HUNTER behavioral hunt packages to identify undetected techniques that incorporate the exploitation of known vulnerabilities.
Tracks vulnerabilities at every stage of their lifecycle and provides timely alerts to any changes in the weaponization and exploitation of a vulnerability, along with observed discussions in the cyber underground. An exploit lifecycle indicator allows you to instantly recognise the threat level associated with a vulnerability and pivot to analyst driven assessments and related intelligence reports to ensure you have all the information you need to prioritize your vulnerability management.
Attack Surface Exposure, our intelligence-led external attack surface management (EASM) solution, helps you discover and identify your internet-facing assets and harness CTI on the threat landscape to prioritize patching and improve your risk-based vulnerability management.
Dashboard to tracks and alerts on state changes across the range of precursors of exploitation, focusing on actual analyst judgements versus monitoring volumetric keyword hits
Delivers vulnerability insights complete with sourcing for deeper context, background on vulnerabilities, and monthly predictive assessments on emerging trends
Monitors threat actor discussions, interest levels, exploit development, and buying/selling activity signaling weaponization and productization is imminent
Identifies key precursors to vulnerability exploitation and tracks the lifecycle of significant vulnerabilities
Provides intelligence reducing signal-to-noise with a focus on the adversary situation
Addresses gaps in current vulnerability offerings, prioritizes remediation efforts and proactively identifies unknown risk
Stay informed with our weekly executive update, sending you the latest news and timely data on the threats, risks, and regulations affecting your organization.