DON’T GIVE THREAT ACTORS THE KEYS TO YOUR KINGDOM
Compromised credentials give cybercriminals the initial access they need into your organization to conduct cybercriminal activity. Verizon's Data Breach Investigation Report 2025 indicates the significant increase in breaches in 2025, and that credential abuse still remains one of the preferred entry points for attackers. The chronic nature attacks via compromised credentials is unsurprising given the increasing digitization of business operations, users’ recycled passwords, and the high value placed on this data on the cyber underground.
When the consequences of a credential-based attack spoil both stakeholder trust and the bottom line, organizations must seek strategies for protecting their credentials against these attacks. Some of the most prevalent methods of attacks used include:
Phishing Campaigns
This is a cost-effective and efficient attack vector. Threat actors contact employees and trick them, possibly by pretending to be a trusted entity or using emotional appeals, to click a malicious link or divulge sensitive information.
Brute Force Attacks
Threat actors use tools which automatically generate passwords, which the actor then works through in a trial-and-error to attempt to access the user account. Users who employ passwords that are lacking in length and complexity are particularly vulnerable to this attack vector.
Insider Threats
Sometimes employees innocently share credentials by not following security policies and protocols, other times disgruntled employees may deliberately steal information and sell it for financial gain or revenge.
Malware
Malware installed on the network can capture credentials unbeknownst to the organization. Keyloggers, for example, can record keystrokes while other malware will take screenshots of login pages and more, giving threat actors the information they need to steal the account information.
SEE THE BREACH, STOP THE ATTACK
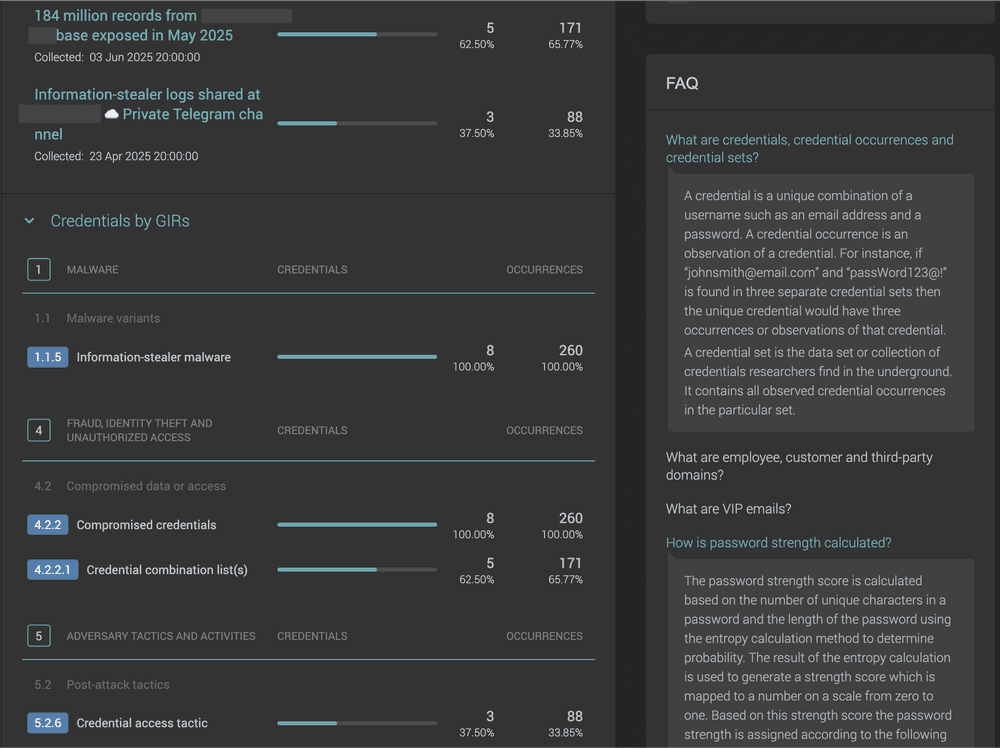
Intel 471 provides organizations the complete visibility of stolen credentials so they can perform remediative action before attackers can use them to fuel cybercriminal activity.
We monitor open sources, underground marketplaces, forums, infostealer logs and alert you as soon as leaked credentials relevant to your stakeholders, including third parties, are identified. We surface what lies unseen for others: our sources embedded deep within “closed” underground spaces will identify and verify when your data is being traded or plans to use your stolen credentials are being discussed. We can perform scans of your external facing attack surface to link compromised credentials directly to exposed assets on your external attack surface.
When action is needed, Intel 471’s timely intelligence on compromised credentials gives you an early signal to investigate. From there, we can support you with relevant threat hunt packages and guidance to help identify and assess any suspicious activity linked to the exposed accounts.
OUTPACE YOUR ADVERSARIES WITH INTEL 471
Comprehensive Visibility:
Intel 471 continuously collects data from tens of millions of data points, including marketplaces, human sources, and infostealer logs.
Fully Contextualized:
We categorize our data and provide the context needed to understand the source of the leak and discern between fresh breaches and older, repackaged data for less false positives for effective mitigation. For example, Infostealers raid computers for valuable data, including login credentials, browser cookies, cryptocurrency wallets, and other financial and system data.
Timely alerts:
Take rapid action to remediate as Intel 471 alerts you on credential exposure across all your stakeholders – your employees, customers, VIPs, and third parties – as soon as they hit the marketplace.
Reduce your attack surface and prioritize action:
Exposure mode not only identifies exposed assets on your external attack surface, such as exposed remote desktop protocol (RDP) that attackers can often use stolen credentials on to gain access, it maps intelligence on compromised credentials directly to any exposures identified.
Hunt for nefarious activity and help respond:
Once accounts are identified as compromised — whether through credential monitoring feeds or internal alerts — we can correlate that intelligence with endpoint behavior by analyzing activity originating from those users to help determine if the compromised account is being actively abused, particularly through post-exploitation behaviors.
Want to learn more about how Intel 471 can help you prevent the compromise of your important credentials?




